Every year, North Korea steals hundreds of millions of dollars in cryptocurrency - not through hacking alone, but by cleaning it up. And the tool they use most? Cryptocurrency mixing services. These aren’t just privacy tools for everyday users. For state-backed hackers, they’re the perfect way to turn stolen Bitcoin into untraceable cash.
What Exactly Is a Cryptocurrency Mixer?
A cryptocurrency mixer, also called a tumbler, takes your Bitcoin or Ethereum and mixes it with coins from dozens or even hundreds of other users. Imagine dumping your cash into a big jar with other people’s bills, then pulling out the same amount - but not your original bills. That’s the idea. The result? Coins that look clean, with no clear link back to you. Mixers work in three steps: first, you send your crypto to the mixer. Second, the service shuffles it with others’ coins using complex algorithms. Third, it sends back the same amount - but to a new wallet you control. The original trail? Gone. That’s why mixers are popular with people who want privacy. And also why they’re perfect for criminals.Why North Korea Loves Them
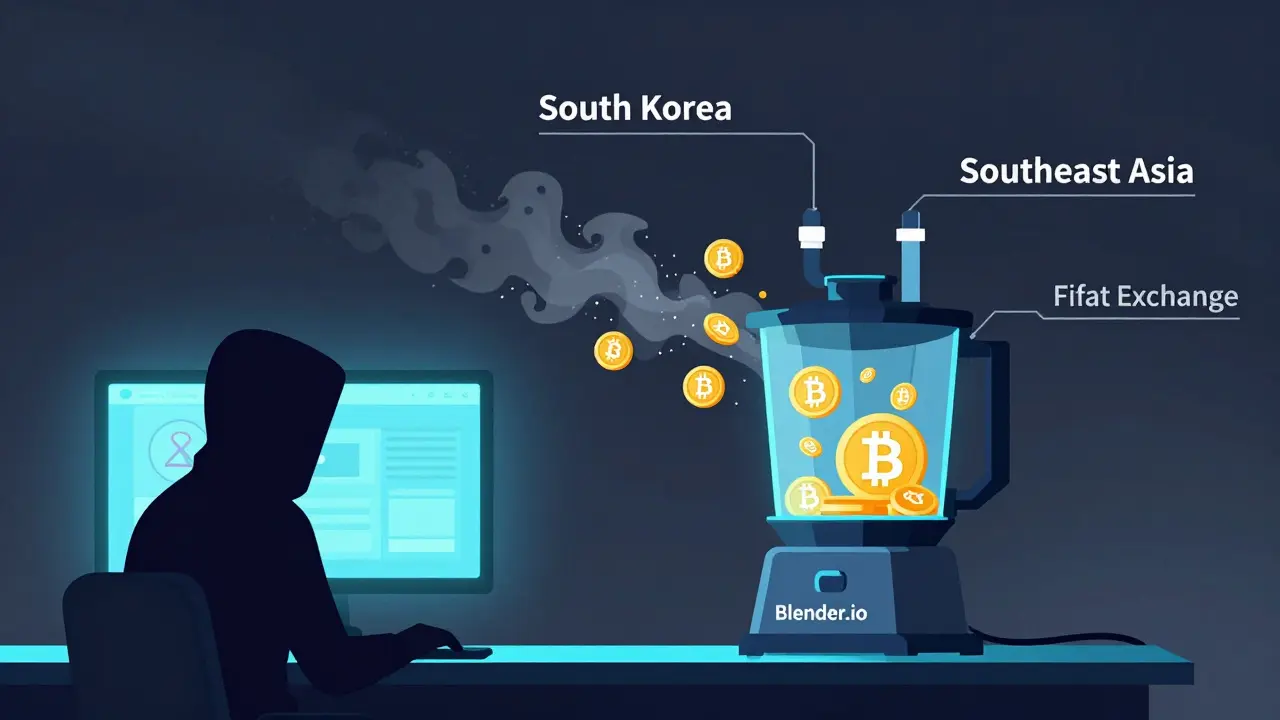
North Korea’s hacking groups - like Lazarus Group - have stolen over $3 billion in crypto since 2017, according to Chainalysis. But stolen coins are useless if you can’t spend them. Exchanges freeze accounts linked to known thefts. Wallets with dirty coins get flagged. That’s where mixers come in. North Korean operators don’t just use one mixer. They chain them. One mixer clears the trail from a hack. A second one breaks the connection further. A third one sends the final clean coins to a converted exchange or peer-to-peer seller. By the time the money hits a bank or fiat wallet, it looks like legitimate income. There’s no public court case proving exactly which mixer North Korea used in each theft. But blockchain analysts have traced patterns. For example, after the $620 million Ronin Bridge hack in 2022, funds flowed through multiple mixers - including Blender.io and Wasabi Wallet - before disappearing into South Korean and Southeast Asian exchanges. The same pattern shows up after the $100 million Harmony Bridge hack, and dozens more.Centralized vs. Decentralized Mixers: Which Do They Use?
There are two types of mixers: centralized and decentralized. North Korea uses both - but for different reasons. Centralized mixers are run by companies. You send your coins to their server. They hold them for a few hours, shuffle them, and send them back. These are faster and easier to use. But they’re also risky. The operator can steal your coins. Or worse - they can keep logs. And guess what? U.S. authorities have shut down several centralized mixers in the last five years. Blender.io, Sinbad.io, and ChipMixer were all taken down after investigations tied them to North Korean laundering. Decentralized mixers are different. They run on smart contracts. No company owns them. No server to hack. No logs to seize. CoinJoin and Wasabi Wallet are examples. These are harder to shut down. And they’re perfect for state actors who want long-term, repeatable anonymity. North Korean hackers use these for ongoing operations because they don’t need to trust anyone. The code does the work.
How Law Enforcement Is Fighting Back
The U.S. Treasury’s Financial Crimes Enforcement Network (FinCEN) now classifies all centralized mixers as unregistered money services businesses. That means operating one in the U.S. is illegal. In 2022, the DOJ indicted four Russians for running Blender.io - even though they never admitted to knowing their users were North Korean hackers. The case relied on blockchain forensics, not confessions. Exchanges are also stepping up. Binance, Coinbase, and Kraken now freeze any wallet that has ever sent funds through a known mixer. They use tools like Chainalysis and Elliptic to flag suspicious addresses. If your Bitcoin passed through a mixer, even once, you might not be able to cash out. But here’s the problem: mixers keep evolving. New ones pop up on the dark web. Others hide behind decentralized apps. Some even use privacy coins like Monero to bridge the gap between Bitcoin and fiat. Law enforcement is playing catch-up.The Bigger Picture: Privacy vs. Crime
Not everyone using a mixer is a criminal. Some people use them to protect their financial privacy - especially in countries with surveillance-heavy banking systems. But when 80% of mixer usage comes from illicit sources - as Chainalysis found in 2023 - the line blurs. North Korea isn’t the only bad actor. Iranian hackers, Russian ransomware gangs, and darknet vendors all use mixers. But North Korea is unique. They’re a nation-state with unlimited resources. They don’t just steal crypto - they’ve built entire teams to launder it. Their goal isn’t just cash. It’s funding nuclear weapons and missile programs. In 2024, the UN reported that North Korea used crypto laundering to bypass sanctions worth over $1.2 billion. That’s more than 10% of their annual GDP. And mixers are the engine behind it.